

点击上方蓝字关注我哦!
序
51%攻击真实的存在
最近有至少五个加密货币在过去一个月里遭受过一次比实际更为理论化的攻击。Monacoin (MONA),比特币黄金 (BTG),zencash (ZEN),Verge (XVG),litecoin现金 (LCC)。
在每种情况下,攻击者都能够获得足够的计算能力来妥协这些小型网络,重新安排他们的交易并以数百万美元潜逃,这可能是银行抢劫案的加密等效。
但更令人惊讶的是,所谓的51%攻击是一个众所周知的危险加密货币攻击载体。
尽管过去有一些这种攻击事件成功地发挥作用,但它们并不是那麽普遍。他们非常罕见,一些技术专家甚至认为某些大型区块链上的矿工永远不会成为受害者。古老的(在加密时间)的论点?这太昂贵了,他们不会从中获得那麽多的钱。但似乎不再是这种情况。
纽约大学计算机科学研究员Joseph Bonneau去年发布了一项研究报告,估计只需租用电力而不是购买所有设备,在顶级区块链上执行这些攻击需要花费多少钱。

他得出的一个结论是?这些攻击可能会增加。事实证明,他是对的。

「一般来说,社区认为这是一个遥远的威胁,我认为这远没有那麽遥远,一直在试图警告风险」
他告诉记者,并补充道:“即使我认为它不会很快开始发生。”
二
在攻击里面
退一步说,加密货币旨在解决一个长期存在的计算机科学问题,称为“双重支出问题”。
基本上,在没有激励计算机监控和防止不良行为的情况下,消息传递网络无法充当货币系统。简而言之,他们不能阻止某人同时花费相同的数据5次甚至1000次(不信任第三方完成所有的肮脏工作)。
这就是他们工作的全部原因,与矿工(表示运行区块链软件所需的机器的术语)消耗电力并确保没有人的钱被盗。
为了使用这种攻击媒介赚钱,黑客需要准备好几件。首先,攻击者在摧毁大部分散列能力时无法做任何他们想做的事情。但是他们能够在特定条件下将花费加倍。
把所有这些昂贵的散列能力都集中在一杯咖啡上花费3美元的交易是没有意义的。如果攻击者能够窃取数千甚至数百万美元的资金,攻击者只能从中获益。
因此,黑客已经找到了各种巧妙的方法来确保条件恰到好处,让他们获得额外的资金。这就是monacoin,比特币黄金,zencash和litecoin现金的攻击者所有目标交易所都拥有数百万加密货币的原因。
通过收集网络散列能力的一半以上,比特币黄金攻击者能够将花费两倍非常高昂的交易花费在交易所上。
通过zencash的三次成功攻击(一种鲜为人知的加密货币,这是一个私密头脑的Zcash分支的一个分支),攻击者能够以当时价值超过500,000美元的大约21,000多个zen(zencash令牌)写作。
尽管攻击者利用不安全的规则将网络混淆为赚钱,但对边缘的攻击有点不同。虽然,很明显攻击是针对边缘的较低协议层的,研究人员正在辩论他们在技术上是否构成51%的攻击。
三
小幣有風險
但是,如果这些攻击在很长一段时间内不常见,为什麽我们突然看到它们的爆发?
研究人员在与CoinDesk的交谈中辩称,没有一个明确的理由。相反,有很多因素可能有所贡献。例如,小硬币并不是巧合,而是被攻击的。由於他们吸引了更少的矿工,因此购买(或租用)建立大部分网络所需的计算能力会更容易。

此外,zencash的联合创始人Rob Viglione认为矿业市场的兴起,用户可以在没有购买的情况下有效租用采矿硬件,设置并运行采矿硬件,使得它更容易,因为攻击者可以用它轻松地购买大量的一次性挖掘能力,而不必花费时间或金钱建立自己的矿工。
同时,随着这些市场积累了更多的散列能力,执行攻击变得更加容易。
黑客现在意识到它可以用来攻击网络
作为一个数据点,有人甚至建立了一个网站Crypto51,显示51%使用采矿市场(在这个例子中,一个叫做NiceHash)攻击各种区块炼是多麽昂贵。例如,攻击比特币可能只需花费719美元就可以使用租用的计算能力进行攻击。
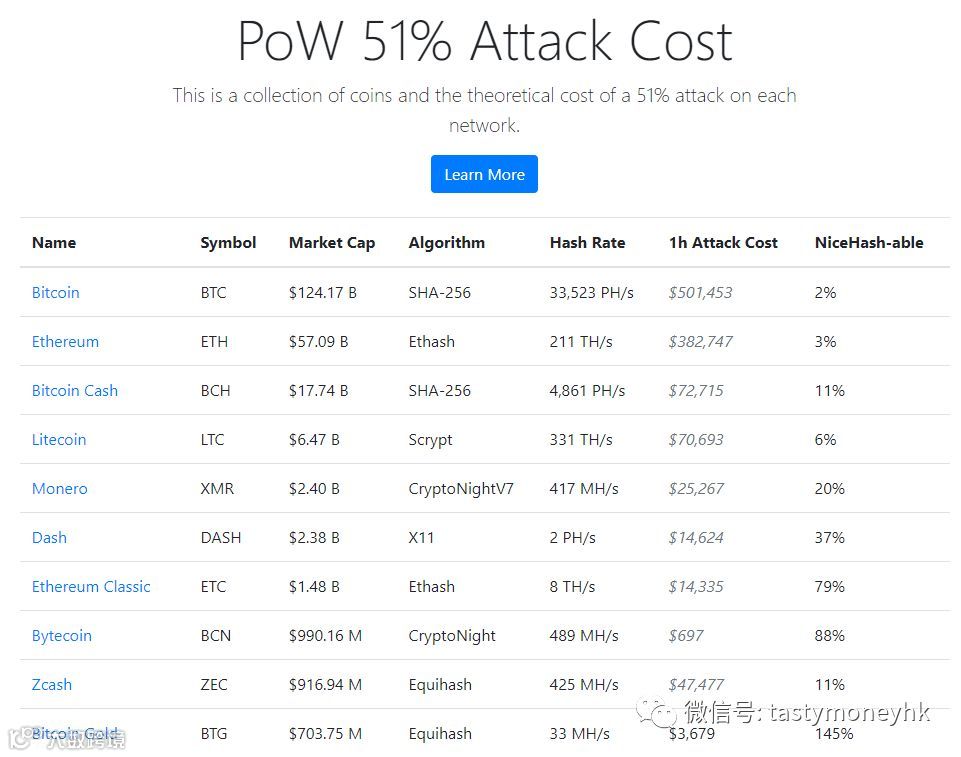
(crypto51:51%攻势所需成本)
康奈尔大学教授EminGünSirer推特说:“如果你的储蓄存在硬币或其他任何东西,每天花费不到100万美元来攻击,你应该重新考虑你在做什麽。”
另一方面,像比特币和以太坊这样的大型加密货币比51%的攻击更难,因为它们要大得多,需要比NiceHash更多的散列功能。
“比特币太大了,没有足够的备用比特币挖掘能力来缓解攻击,”Bonneau告诉记者。
但是,虽然Crypto51给出了一个粗略的估计,但苏黎世联邦理工学院的研究Arthur Gervais认为,这样做的结果是一丝不漏,因为它“忽略”了购买硬件和软件的初始成本。 “因此,我脑海中的计算过於简单,”他补充道。
四
解决方案:更长时间的等待
Gervais进一步认为将这些攻击置於上下文中是值得的。虽然51%的攻击可能是最着名的加密货币攻击,但这不一定是他心中最糟糕的。
他指出了其他恶意bug,比如在zcoin中发现的bug,如果被利用,用户可以根据需要打印尽可能多的zcoin。但是51%的攻击仍然令人困扰,因为它们有时候还是值得的,影响交易所或碰巧在攻击者的十字准线中。
“作为一个行业,我们必须结束这种风险,”Viglione说,指出zencash努力阻止这种情况再次发生。
无论哪种方式,用户或交易所确保他们没有被欺骗的一种方式是只接受年龄较大的货币,或者被更多的交易块所掩盖,称为“确认”。越来越多的证据表明,这笔资金将以51%的比例被偷走。
最初,比特币黄金被盗的交易所只需要五次确认,攻击者可以用他们的散列能力将其全部撤回。作为对这些攻击的回应,他们已经将确认数量提高到50个,至少目前为止,已经成功阻止了这些攻击。
正因为如此,开发人员和研究人员认为更大的区块链以及更多的散列能力更安全,因为它们需要更少的确认。
正如比特币企业家John Light所说的那样:
记住,下次有人告诉你他们使用altcoins,因为他们'使用便宜'。
原文来至CoinDesk
https://www.coindesk.com/blockchains-feared-51-attack-now-becoming-regular/
Blockchain's Once-Feared 51% Attack Is Now Becoming Regular
Monacoin, bitcoin gold, zencash, verge and now, litecoin cash.
At least five cryptocurrencies have recently been hit with an attack that used to be more theoretical than actual, all in the last month. In each case, attackers have been able to amass enough computing power to compromise these smaller networks, rearrange their transactions and abscond with millions of dollars in an effort that's perhaps the crypto equivalent of a bank heist.
More surprising, though, may be that so-called 51% attacks are a well-known and dangerouscryptocurrency attack vector.
While there have been some instances of such attacks working successfully in the past, they haven't exactly been all that common. They've been so rare, some technologists have gone as far as to argue miners on certain larger blockchains would never fall victim to one. The age-old (in crypto time) argument? It's too costly and they wouldn't get all that much money out of it.
But that doesn't seem to be the case anymore.
NYU computer science researcher Joseph Bonneau released research last year featuring estimates of how much money it would cost to execute these attacks on top blockchains by simply renting power, rather than buying all the equipment.
One conclusion he drew? These attacks were likely to increase. And, it turns out he was right.
"Generally, the community thought this was a distant threat. I thought it was much less distant and have been trying to warn of the risk," he told CoinDesk, adding:
Inside the attacks
Stepping back, cryptocurrencies aim to solve a long-standing computer science issue called the "double spend problem."
Essentially, without creating an incentive for computers to monitor and prevent bad behavior, messaging networks were unable to act as money systems. In short, they couldn't prevent someone from spending the same piece of data five or even 1,000 times at once (without trusting a third party to do all the dirty work).
That's the entire reason they work as they do, with miners (a term that denotes the machines necessary to run blockchain software) consuming electricity and making sure no one's money is getting stolen.
To make money using this attack vector, hackers need a few pieces to be in place. For one, an attacker can't do anything they want when they've racked up a majority of the hashing power. But they are able to double spend transactions under certain conditions.
It wouldn't make sense to amass all this expensive hashing power to double spend a $3 transaction on a cup of coffee. An attacker will only benefit from this investment if they're able to steal thousands or even millions of dollars.
As such, hackers have found various clever ways of making sure the conditions are just right to make them extra money. That's why attackers of monacoin, bitcoin gold, zencash and litecoin cash have all targeted exchanges holding millions in cryptocurrency.
By amassing more than half of the network's hashing power, the bitcoin gold attacker was able to double spend two very expensive transactions sent to an exchange.
Through three successful attacks of zencash (a lesser-known cryptocurrency that's a fork of a fork of privacy-minded Zcash), the attacker was able to run off with about more than 21,000 zen (the zencash token) worth well over $500,000 at the time of writing.
Though, the attack on verge was a bit different since the attacker exploited insecure rules to confuse the network into giving him or her money. Though, it's clear the attacks targeted verge's lower protocol layer, researchers are debating whether they technically constitute 51% attacks.
Small coins at risk
But, if these attacks were uncommon for such a long time, why are we suddenly seeing a burst of them?
In conversation with CoinDesk, researchers argued there isn't a single, clear reason. Rather, there a number of factors that likely contributed. For example, it's no coincidence smaller coins are the ones being attacked. Since they have attracted fewer miners, it's easier to buy (or rent) the computing power necessary needed to build up a majority share of the network.
Further, zencash co-creator Rob Viglione argued the rise of mining marketplaces, where users can effectively rent mining hardware without buying it, setting it up and running it, has made it easier, since attackers can use it to easily buy up a ton of mining power all at once, without having to spend the time or money to set up their own miners.
Meanwhile, it's grown easier to execute attacks as these marketplaces have amassed more hashing power.
"Hackers are now realizing it can be used to attack networks," he said.
As a data point for this, someone even erected a website Crypto51 showing how expensive it is to 51% attack various blockchains using a mining marketplace (in this instance, one called NiceHash). Attacking bytecoin, for example, might cost as little as $719 to attack using rented computing power.
"If your savings are in a coin, or anything else, that costs less than $1 million a day to attack, you should reconsider what you are doing," tweeted Cornell professor Emin Gün Sirer.
On the other hand, larger cryptocurrencies such as bitcoin and ethereum are harder to 51% attack because they're much larger, requiring more hashing power than NiceHash has available.
"Bitcoin is too big and there isn't enough spare bitcoin mining capacity sitting around to pull off the attack," Bonneau told CoinDesk.
But, while Crypto51 gives a rough estimate, ETH Zurich research Arthur Gervais argued to take the results with a grain of salt, since it "ignores" the initial costs of buying hard and software. "Thus, the calculations are oversimplified in my mind," he added.
The solution: a longer wait
Gervais further argues it's worth putting these attacks into context. Though a 51% attack is perhaps the most famous cryptocurrency attack, it's not necessarily the worst in his mind.
He pointed to other malicious bugs, such as one found in zcoin, where, if exploited, a user would have been able to print as many zcoin as they would like. But 51% attacks are still troubling since they can still be worthwhile sometimes, impacting exchanges or whoever happens to be in the crosshairs of the attacker.
"As an industry, we have to put an end to this risk," Viglione said, pointing to efforts on zencash to stop this from happening again.
Either way, one way for users or exchanges to make sure they aren't defrauded is to only accept money that's older, or has been buried by more blocks of transactions, called "confirmations." The more confirmations there have been, the harder the funds are to steal in a 51% attack.
Initially, exchanges where bitcoin gold was stolen required only five confirmations, and the attacker was able to reverse all of them with their hashing power. In response to the attacks, they have upped the number of confirmations to 50, which has successfully plugged up the attacks, at least for now.
Because of this, developers and researchers contend bigger blockchains with more hashing power behind them are more secure since they require fewer confirmations.
As bitcoin entrepreneur John Light put it:
【欢迎读者朋友投稿分享,投稿邮箱:articles@tastymoney.hk 】

添味财经简介︰
我們是一个免费的财经资讯平台, 由阿法牛传媒有公司创办,
目前添味财经节目主要定位为港股市场。
网页: www.tastymoney.hk
电邮: alphabull.tv@gmail.com
电话: +852 6633 4386
欢迎读者朋友投稿分享
投稿邮箱:Articles@tastymoney.hk

免责声明
投资涉及风险,文中内容仅代表作者个人观点,请读者仅作参考,并请自行核实相关内容。文章内容不构成买卖任何投资工具或者达成任何交易的推荐,不构成投资建议投资咨询意见或其他意见。







