坦然应对泄露事件:网络恢复分步计划


















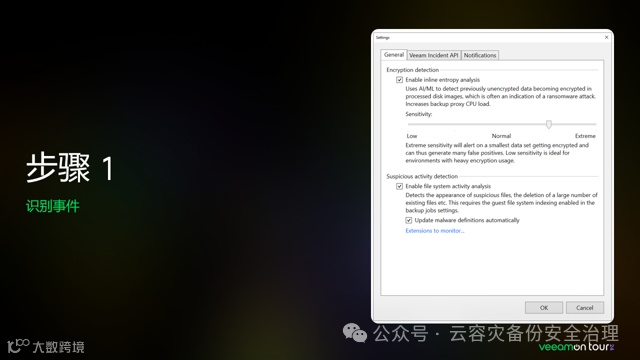



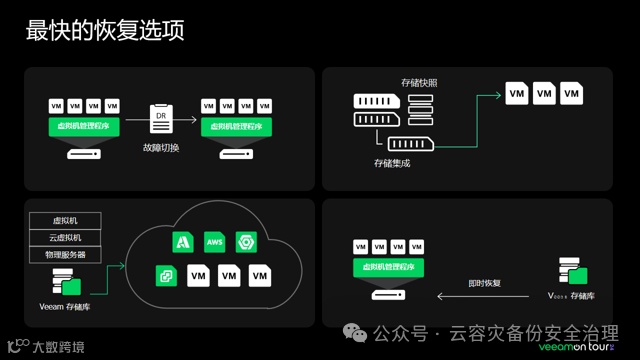




附相关的资料网址为:
https://www.veeam.com/blog/zero-trust-data-resilience.html
Understanding Zero Trust Data Resilience (ZTDR)
Why Zero Trust?
In the modern IT landscape, users must be able to access data from anywhere. However, this has created significant challenges for the traditional networking security models that attempt to build secure perimeters and keep threats out. As users and data have become more distributed over time, it’s becoming clear that this model is no longer sufficient because users access data from all types of networks that cannot be fully secured.
Virtual private networks (VPNs) offered some protection, allowing users outside of the secure perimeter to access data by building a secure tunnel from their system into the secure perimeter. That said, VPNs are not perfect. Beyond basic usability challenges, they still offer a variety of paths for attackers to breach the perimeter. The more distributed users and sites leveraging VPNs, the higher the risk.
The Zero Trust model grew from recognizing that creating fully secure perimeter networks is simply not possible, and therefore, security must evolve to be more explicit. This new model states that, rather than assuming that specific networks are secure, users should assume that all networks are insecure. This is called “assume breach.” Effectively, this means that you should have “Zero Trust” that a connection coming from any network endpoint is a valid one without taking additional validation steps.
This validation can come in various methods and implementations, but should generally follow these core Zero Trust principles:
Least-privilege access: Access is restricted to what’s essential at the right time and with just enough access. This prevents lateral movement and unauthorized access to other network parts.
Verify explicitly: Departing from traditional “trust but verify” methods, this principle focuses on always authenticating and authorizing by using available information like user identity, location, devices, workload, data, etc.
Assume breach: Operating under the assumption that breaches will happen, Zero Trust prioritizes detection, response, and rapid recovery to minimize the impact of security breaches and the subsequent blast radius.
What is Zero Trust Data Resilience?
Zero Trust has historically been applied to an organization’s entire ecosystem but their backup environment. This is a problem since, as we know, it’s now not a matter of if but when an organization will be impacted by cyberattacks like ransomware. Veeam’s Zero Trust approach, Zero Trust Data Resilience (ZTDR), focuses on expanding Zero Trust principles to include an organization’s backup environment. This philosophy is foundational to our approach to data protection and an organization’s cyber resilience strategy.

The core principles of Zero Trust Data Resilience are key elements in protecting your data:
Separation of backup software and backup storage: Minimize attack surface and blast radius
Multiple resilience zones: 3-2-1 backup rule
Immutable and encrypted backup storage: Protect backup data from modification or deletion
.......................................
Immutable and Encrypted Backup Storage
The final core principle of ZTDR is immutability and encryption. Backups are only good if you can restore them when needed, so the integrity of your data should be made a priority for your data protection and backup admins.
Immutability means that something that was once written is now unable to be altered or deleted. Specific to data protection, immutability means backups can only be deleted once a set period of time has expired, and is therefore safe from potential changes, including accidental and intentional deletion. Immutability should be implemented across all resilience zones regardless of where data is stored, including primary backup, secondary backup, cloud, tape, etc.
Any repository that’s critical in an incident response and recovery plan should implement immutability. It’s important to note that destruction or malicious encryption of data also makes data unavailable, and immutability can help ensure the availability of your backup data as well.
Immutability and air gapping doesn’t protect confidentiality, however. Fortunately, encryption is a double-edged sword that makes data unreadable by anyone without the key, which locks cybercriminals out of backups. This greatly reduces the risk of data exfiltration, espionage, and reconnaissance.
An important element of encryption for cybersecurity programs is the use of centralized key management systems (KMS). Utilizing a KMS to encrypt Veeam backups is a simple implementation task that allows security team to manage and protect the keys that will allow users to decrypt backup data.
Encryption should be applied everywhere, since accessing any single copy is enough to cause a data leak. However, encryption doesn’t prevent destruction or another layer of encryption, so it can’t help to ensure integrity and availability. By implementing both immutability and encryption on top of an air-gapped implementation, customers can take a layered approach to achieving the CIA Triad.



